
Why Small Businesses Are The Most Vulnerable from Ransomware Attacks
Posted on February 4, 2020 in Data Breach, IT Security, IT Security Assessment
Ransomware: Why Small Businesses are the Most Vulnerable
In recent years, a rash of high-profile ransomware attacks have left many businesses with the impression that only big organizations need to protect themselves from cybercriminals. The truth is exactly the opposite. In reality, small businesses are more often the victims of ransomware attacks—and no business is too small to become a target. Is your business protected?
Why are Small Businesses Targeted by Ransomware Attacks?
The term malware—malicious software—refers to any kind of software that was created with the intent to do harm. Some focus on stealing personal information to try and gain access to financial accounts. Others are designed to simply cause havoc in the systems they infect.
Ransomware is a specific category of malware with a different kind of objective. Instead of stealing account information or data, ransomware locks or encrypts files so that the owner can’t access them. The ransomware also gives instructions on how to pay a ransom in exchange for a password to decrypt or regain access to the files. Ransomware is evolving, of course, and now, some versions do more than just encrypt data. Some new strains of ransomware allow hackers to upload your data to their own server, as well as encrypt it in its original place
More recently, the city of Baltimore fell victim to a ransomware strain known as RobbinHood2. On May 7, 2019, city government computers were infected and taken offline by an unknown hacker group that demanded a Bitcoin ransom worth over $75,000. The city was unable to restore its systems until May 20, affecting email, payment systems, and even the city’s real estate market. Baltimore was previously hit in 2018, when hackers infected the city’s 911 system and forced a temporary system shutdown.
Attacks like these contribute to the belief that small businesses are safe from cyberattacks, but this couldn’t be further from the truth. In 2018, 71% of ransomware attacks targeted small businesses, with those in the healthcare sector hit the hardest. And ransomware attacks are on the rise, with an 11% increase from 2017 to 2018.
Few Small Businesses are Equipped to Deal with Ransomware
Small businesses are the most common targets of ransomware attacks. And unfortunately, they also tend to be hit the hardest by them—if not in the size of the ransom demand, certainly in terms of the organization’s ability to deal with the attack and its consequences.
One reason for this is simply that small business owners tend to believe that the size of their business makes them unlikely to be a target. Therefore, they don’t put as much effort into security as a larger business might. They’re also unlikely to have a plan in place to deal with the aftermath of a cyberattack. If they get hit, they struggle to deal with the fallout.
The second reason why small businesses are more vulnerable is that they don’t invest in cybersecurity. They don’t have the budget to employ an IT team, or buy expensive equipment. And many forgo security altogether, instead of searching for more affordable solutions.
How can You Protect Your Small Business?
As a small business owner, there’s a lot you can do to protect your business from ransomware and other malware attacks, even on a small budget.
Be Smart and Safe Online
According to Verizon’s 2019 Data Breach Investigations Report4, email is the most common method way for malware to access a system. And, over 80% of malicious emails use phishing activity to steal sensitive information or get the user to download malware to their computer.
While some security practices involve a financial outlay, one of the most effective methods of improving your security is free. Teach your employees how to stay safe online, and you can greatly reduce the risk that your computer system might become compromised. For instance:
- Use multi-factor authentication when logging in to email and other accounts. This means using two or more methods of verifying identity, such as a password plus a code sent to your mobile phone at the time of login.
- Don’t click on links or download attachments until you’ve verified their safety. If you know the sender, call them to check. If you don’t know the sender, scan the email for signs of phishing.
- Phishing emails use a variety of tricks to get people to click links or download attachments. These include suspicious activity warnings, requests for information or verification, offers of prizes or discounts, or payment requests.
- Phishing emails often claim to be from large brand-name companies such as Facebook, PayPal, or Netflix. But a close read of the email shows signs like poor spelling or grammar, or a generic greeting such as “Dear Customer”, that indicate it’s not what it seems.
- Phishing emails often use sender addresses that are similar to legitimate business email addresses, but aren’t exactly the same. For instance, “paypal12.com” instead of “paypal.com”. Check the sender address by hovering the cursor over it in the email, to verify the sender’s domain.
- Be particularly cautious with unsolicited email, or email from an unknown sender, especially if there are requests for sensitive information.
When in doubt, always check with the sender of the email, even if it’s from a co-worker. A new kind of phishing, dubbed spear-phishing, targets employees with the specific intent of gaining information that can be used to access sensitive company systems or data. These emails tend to be more sophisticated than the average phishing attempt, so it’s important to read with a critical eye.
Outsource Your IT Needs
If, like many small business owners, you haven’t given much thought to security before, now may be a good time to start! You may not have the budget for an IT team, but there are other options.
For small businesses, a simple and affordable solution is to outsource security to a third-party provider. By outsourcing security services, you benefit from advanced protection without a big financial outlay.
Backup Your Data
Even the most sophisticated security can’t guarantee your safety 100%. But if your data is regularly backed up, you can survive any cyberattack. One option is to use an online backup service that saves all your data in an offsite location. If your business is attacked, you can use the backups to restore your files, without having to resort to paying a ransom.
Your Small Business May Be Vulnerable, But You Can Protect It
Ransomware is a potentially significant threat, especially for small business owners. However, there’s a lot you can do to reduce your level of risk. By educating your employees and outsourcing security services, you can help ensure that your business doesn’t become a target.

JLKTech-EmailPhishing
Posted on April 3, 2018 in Data Breach, IT Security, IT Security Assessment, Secure Email
Late last week, CareFirst BlueCross BlueShield said that it was the victim of a data breach which potentially exposed the personal information of 6,800 of its members including names, member identification numbers and dates of birth. In eight cases, social security numbers could have been exposed.
CareFirst believes the breach was the result of an email “phishing” scheme. Phishing attacks use deceptive emails and websites to convince people to disclose personal information. Phishing has become one of the most pervasive problems facing data security staffs today. Generally speaking, a basic phishing attack is relatively easy to conduct and inexpensive for the attacker.
Our Checklist:
When you are going through your email and before you click that link, consider these rules of thumb before opening or clicking any links.
- Does the email ask for personal or sensitive information, such as your date of birth, Social Security number, an account number or login credentials? Most legitimate businesses do not request such data in an email.
- Does the email asks you to click on a link to access a web site? If so, that site might be fake.
- Does the email have a generic salutation rather than your name? Your bank or service provider know who you are and normally will address you by name.
- Does the email have an attachment? If you are not expecting an attachment, don’t click on it. Confirm its validity first with the sender.
- When you move your mouse over the email, is the entire email a hyperlink? If so, it likely is a phishing attack.
- If the email makes an offer too good to be true, such as a large sum of money, a prepaid gift card or an expensive piece of electronics for free, it’s likely a phishing attack.
- Be careful of emails that make an emotional plea while asking for money. While many charities use such tactics, it also is a popular approach used by phishers.
- If the email claims you have an immediate problem, such as a virus or that you are running out of email storage space, and you must take immediate action, be careful. This is a common phishing tactic.
- If the email makes a direct threat and requires that you take immediate action by clicking a link for the IRS, a police agency or the like, it’s probably fake.
- An email might appear to be from a friend asking for money. Never send money without calling the friend first to confirm the request.
Find out just where you are with your tech. Technology should never be considered a “set it and forget it” part of your business. It takes constant tweaking, monitoring and maintenance to make your system reliable. You should strongly consider having a formal IT Security Assessment performed on your system no matter how large or small your business is as these formal scans can give you an excellent chance to find out just where you have vulnerabilities.
We can assist you with any of the above protection measures mentioned above. It is far less costly to be proactive than it is to be reactive. NOW is the time to find out, not later or even worse… after!

5-Scariest-Security-Threats-2018
Posted on January 29, 2018 in Data Breach, IT Security, IT Security Assessment
The information security threat landscape is constantly evolving, but it’s not getting any less complicated. In 2017, Ponemon Institute research revealed that 1 in 4 businesses in the U.S. suffered a security breach. Threats aren’t equally distributed by business size, 50 percent of small businesses were targeted by hackers and health care organizations were also heavily-targeted by 15 percent of last year’s incidents.
Recent headlines have revealed plenty of scary threats, including ransomware epidemics and the emergence of wiper viruses. While it’s possible 2018 has new super threats in store, it’s likely you’ll face a well-established threat. From social engineering to weak passwords, you may be surprised by today’s most common information security threats.
1. Crimeware-as-a-Service
Some of today’s smartest hackers are selling ready-made crimeware to wanna-be hackers on the dark web by subscription, including malware-as-a-service and ransomware-as-a-service. Last year, 51 percent of security breaches involved malware, which can now be purchased through illegal channels for just several hundred dollars each month. Criminals are getting bolder–one pre-packaged threat called “Philadelphia” was recently advertised openly on YouTube.
2. IoT Vulnerabilities
Experts predict one of the worst trends in 2018 will be security vulnerabilities caused by connected internet of things (IoT) devices. InfoSecurity Magazine’s Tara Seals attributes this to the fact too many “devices are manufactured without security regulations or industry standards.”
If your business isn’t powered by high-tech sensor or beacons, you’re not necessarily in the clear. IoT devices include office technology. Like IP phones, printers, and routers–all of which could represent possible modes of entry into your company’s network. In one survey, 63 percent of companies admitted to a printer-related security breach.
3. New Compliance Requirements
If your company collects data on European Union Citizens, you’ll need to prepare to comply with the General Data Protection Regulation (GDPR) by May or face fines of €20 million–that’s approximately $24.3 million. Many companies will need to adjust processes and systems to meet requirements from the GDPR, PCI, HIPAA, or other legislation.
While compliance isn’t a threat, it plays an important role in discussions of information security. Just 28.6 percent of companies are still compliant a year after assessment, and failing to meet standards can indicate security risks. Compliance can also demand significant IT resources. If your company is struggling to balance compliance and cybercrime risks, you may need security help.
4. Password Theft
A staggering 81 percent of 2017 security incidents involved weak or stolen passwords, which was often combined with tactics like phishing, hacking or malware. One emerging trend is “password aftershock“–when hackers are able to successfully gain entry to a company’s network using username and password combinations stolen from other breaches due to people’s tendency to recycle the same passwords over and over again.
5. Email Risks
Phishing still works–66 percent of installed malware last year was delivered by an email. Hackers are getting savvier and increasingly employing techniques like social engineering to “spoof” malicious emails into appearing like they were sent by a colleague or personal friend.
Email is a critical business communications tool, but it’s also one of the easiest ways for hackers to get inside your network. Information security awareness training and testing are likely a necessity.
Conclusion: Are You Prepared for These Security Threats?
While 2018 could bring next-generation security risks, businesses are wise to take a look back at the most common threat trends that affected half of small businesses in 2017. Planning for the most common risks–like unsecured printers, weak passwords and phishing–could significantly mitigate your chances of suffering a data breach in 2018.
Avoid the costly impact of a security breach remediation with a complimentary assessment of your organization’s IT security. Click here to learn more.
Sources
- https://securityintelligence.com/know-the-odds-the-cost-of-a-data-breach-in-2017/
- https://www.cnbc.com/2017/04/05/congress-addresses-cyberwar-on-small-business-14-million-hacked.html
- http://www.verizonenterprise.com/verizon-insights-lab/dbir/2017/
- https://www.darkreading.com/threat-intelligence/the-rising-tide-of-crimeware-as-a-service/d/d-id/1329102?
- https://nakedsecurity.sophos.com/2017/07/25/ransomware-as-a-service-how-the-bad-guys-marketed-philadelphia/
- http://quocirca.com/content/print-security-cost-complacency-121
- https://www.gdpr.associates/what-is-gdpr/understanding-gdpr-fines/
- http://www.verizonenterprise.com/resources/report/rp_pci-report-2015_en_xg.pdf
- https://www.bna.com/people-dont-seem-b73014447747/
Posted on May 9, 2016 in IT Security, IT Security Assessment

This question can be easily answered be asking yourself if you have not had one performed for you in the last year or ever. If that is the case, the answer would be unequivocally YES!
IT and computers, like many other facets of your business, are not “set it and forget it” devices like a fax machine or a stapler. IT systems have changes being made to them on a daily basis and must have regular attention paid to them in order to keep them from harm’s way and your system running smoothly. Just because something terrible has not happened to your IT systems yet does not mean that your system is forever free and clear and does not need any attention. It really means that you been dodging the bullet and the inevitable significant “game-changer” is not far around the corner.
The most common items that are overlooked on a network / IT system and which can cause major issues are user password policy (passwords not set to expire on a regular basis, not required to be 7 characters or better), system security updates policy (is there an actual plan for regular deployment of updates?) and end-user awareness training. Believe it or not, not addressing or forgetting about these mundane items are what the Internet “bad guys” are hoping for. These are the sort of vulnerabilities that they love to see—old user accounts not disabled, users with easy to guess passwords and in the case of MedStar Health—an unpatched network server and workstation.
You may be saying to yourself that “we are just a small entity” no one wants our data or information.” On the Internet, however, your network is just a number (IP address) much like a house address is to the post office. Your “house” has windows and doors which are called ports.
Do you even know where your Internet firewall is located in your office and how do you know whether your Internet protection device is up-to-date with the latest security firmware updates?
Of the most important security devices in your office should not go unchecked for months or even years. You should keep this unit up-to-date with a support contract from the vendor and by applying regular firmware updates. Having it tested with an external penetration test is equally important.
How old it is or is it even a supported device with the hardware manufacturer any longer?
Your security appliance / firewall should be replaced as often as a desktop computer – every three years or so to ensure that you are taking advantage of the latest security and protection technologies.
Internet ports are only a small fraction of the way risks can be introduced into your network.
Other items at which to look are (and there are MANY more than these):
Poor Data Backup Strategies / Disaster Recovery
Is there even a plan to test the backups or a plan to recover from a significant IT security event? You should have a layered approach to data backup and it should be automated, not manual, and should also include some sort of disaster recovery data restore option.
Remote Access / Employees in the Field / Cloud Computing
Are users in the field or working from home offices updated on a regular basis? Are they using public hot-spots for Internet access? Data in the cloud seems nice and convenient but who is looking at your data as it resides on the vendor’s servers? Have you reviewed your service level agreement with your vendor? What happens if they have a “gotcha” virus moment like a large entity like MedStar? How long does it take to get your data back if the vendor gets bought out by another company and the new company discontinues your cloud offering as a way of killing the competition?
Your business should have a well thought out and concise remote access policy for remote users and the computers that they use should be company-owned so that your IT personnel can dictate security policy on them.
Smart Phones
Is there a company-wide policy for use of smart-phones and remote data sync? Do the phones even have the security lock feature turned on? On an iPhone, if not, the data on the phone is NOT encrypted. Same as with remote computer users, the smartphones that your company employees use should be company owned and administered. You cannot tell your employees to be smart and security aware if you do not own it.
Disgruntled Employees
Is there an employee who is not happy about not getting a promotion? Did he /she have a greater level of data security access than they should have given their job description? Threats from within should be of great concern. You need to keep your finger on the pulse of your staff and to have formal policies as to what needs to be done from an IT perspective before you make someone an ex-employee.
So, to answer the question presented to you at the beginning of this post, “How do I know if my company needs a computer IT Network Security Assessment?” With all of the moving parts of an IT system, the better question is, “Can I afford not to?”
Posted on April 20, 2016 in Data Breach, IT Security, IT Security Assessment
And why it could easily happen to your practice or business
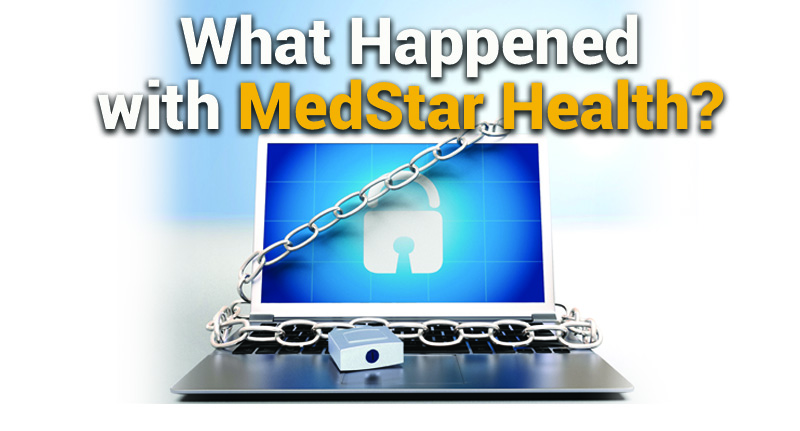
Despite MedStar undoubtedly having a very large IT cybersecurity budget, they still fell victim to a ransomware virus allegedly after an employee clicked on a link in an email. The chain of events found its way to an unpatched Linux server that had a security vulnerability on it that dated all the way back to 2008. The Linux software manufacturer developed and supplied a fix for the security issue shortly after it was discovered in the same year, but MedStar’s technical support team left it unpatched.
That leads me to ask—how many machines are still left without the proper security updates applied at their locations but more importantly at your location? Any single workstation, much less a server, can have over a dozen pieces of software that need to be constantly updated. From Adobe Reader, Adobe Flash Player, Java, and Microsoft Office (only to name a few), there are always security flaws and vulnerabilities that are realized by the software vendor who subsequently issues a fix in the form of a download. Most of these downloads have to be downloaded and applied manually. So, if you have a small practice or business without a dedicated technical person looking for these types of issues, you should ask yourself who is making sure that these updates and being applied and that they are current?
Another question that needs to be answered about the MedStar event is why it took so long for MedStar to restore their data and have their systems back online. Reports have suggested that it took close to a week for that to happen. One would imagine that MedStar would have state-of-the-art data backup systems with multiple options for restoration. The best way to combat a ransomware virus is to accept that you had weaknesses in your cyber-defenses and concede that you had a “they got me” moment and do not pay the ransom but rather move on to the data restoration process as soon as possible. With the correct layer of backups, your server should be able to be restored in time measured in hours not days.
Questions to ask yourself about your small medium-sized business or medical practice IT system:
- Is my front-end security in place?
- Is my firewall current and does it have the latest firmware updates applied?
- Do all of my servers and workstations have the LATEST anti-virus version and definition updates applied?
- Are my data backup systems current and operational?
- Is my data backup an automated process or does it rely on a person to manually perform this function?
- Has my data backup actually been tested to see if it can restore the files that I need restored?
- Is there a layered approach to my backups?
- Do I have an off-site data restoration option in the event that there is a major catastrophe at my place of business?
- Have my employees / end-users been educated on what to do and not to do when using company IT systems?
- Do I have an IT manual that outlines what is expected of my employees as it relates to the IT systems?
- Is there a formal disaster recovery plan in place that details the steps to take to recover from a significant IT security event?
- If you answered “no” to any of the above questions, then it’s time to make a change regarding your IT system management.
If you have questions about this article, please contact Dave Thomas, Director of Technology Services, Kenneally Technology Services, 443.829.9897, dthomas@jlktech.com.










